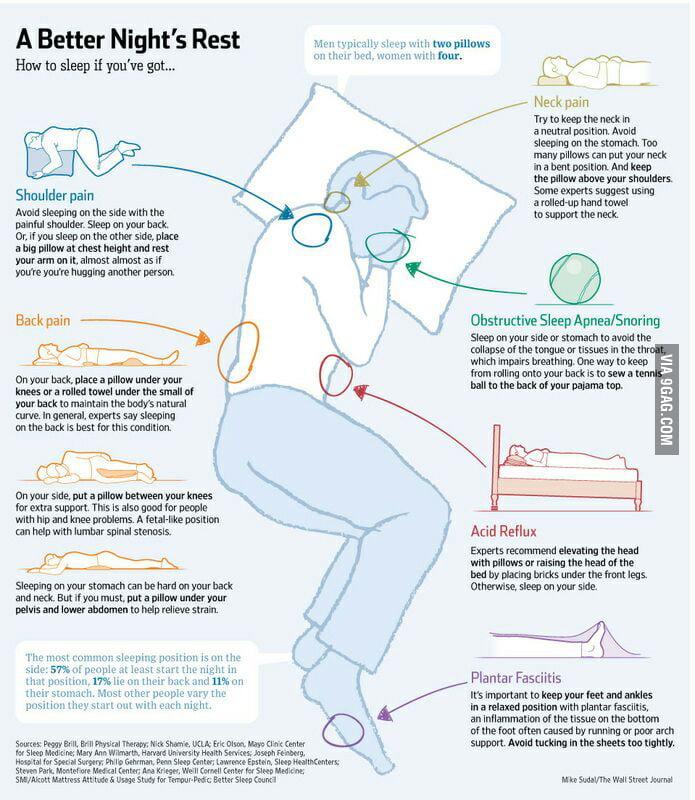
Best ways to prevent burglary
Home burglary: Common tricks burglars use and how you can prevent break-ins
If you're worried about having your home broken into, you're not alone. According to a recent study by Safewise, burglary is the most feared property crime. And that fear isn't baseless: statistics from the FBI show that break-ins are common occurrences in the US, with more than 1.1 million burglaries in 2019. Some might be surprised to learn that more burglaries occurred during the day than at night. The average loss from those burglaries was $2,661.
To understand how and why burglaries happen -- and how you can help prevent them -- I talked to James Lynch, a professor and former chair of the Department of Criminology and Criminal Justice at the University of Maryland. Many of the insights he provided were surprisingly simple and helpful.
Here's how burglars break into homes, and how to help limit the risk of being burglarized.
Most common methods burglars use to break in homes
While it may sound simple, the most common way burglars enter homes is through an unlocked door or window. This is according to a survey of 86 inmates convicted of burglary, conducted by KGW-TV in Portland, Oregon.
"Professional burglars who have some skills will pick a target not just because it's vulnerable, but also because it's more likely to have the type of belongings that could easily be turned into cash," Lynch said.
"If there's evidence of affluence, where a burglar could get a good return on their investment, that type of home will attract burglars," Lynch continued. "But it depends on the burglar's level of sophistication. Some will go around without much planning and try doors until they find one that's open."
When doors and windows were locked, burglars surveyed said they preferred kicking in the door as opposed to breaking a window. Kicking a door in makes less noise than broken glass and doesn't pose a safety risk to the burglar.
Single-family homes in the middle of the street are more likely to be broken into than homes on the corner. This may be due to the greater visibility corner homes have. Conversely, in apartment buildings, Lynch pointed out that corner units with two sides of exposure have a greater likelihood of getting hit than units with only one side of exposure.
Conversely, in apartment buildings, Lynch pointed out that corner units with two sides of exposure have a greater likelihood of getting hit than units with only one side of exposure.
Studies in the UK point to a pattern of repeat victimization. "If you were burglarized once, there's a good chance you'll be burglarized again within the next 10 days," said Lynch. "There are two theories on this pattern. One is the burglars saw something they couldn't take the first time so they come back for it. The second is they've already found a way to gain entrance or get past your security and they want to capitalize on that before you have a chance to repair your door or window."
This pattern holds for near-repeat victimization. For instance, if the house next door gets burglarized, the probability of your house getting burglarized increases, according to Lynch.
"These patterns are consistent with burglary as an occupation," Lynch said.
In addition to doors and windows, accessing your home through your attached garage is another method burglars use. People often leave the door from the house to the garage unlocked and may not be as diligent about securing garage windows and walk-in doors.
People often leave the door from the house to the garage unlocked and may not be as diligent about securing garage windows and walk-in doors.
Simple as it seems, locking your door is one of the easiest ways to protect your house from break-ins.
Tyler Lizenby/CNETHow you can stop home break-ins from happening to you
There are several steps you can take to protect your home, loved ones and belongings from burglars. But the most important step is to secure your doors and windows.
Locks
As simple as locking doors and windows sounds, a survey by YouGov showed that 7% of Americans surveyed do not lock their doors when they go out, and 23% do not lock them when they're home. Locked doors and windows provide an added deterrent for break-ins.
"If people would just lock their doors and windows, that would prevent a lot of burglaries," Lynch said.
Another tip is to rekey your locks when you first move in: You don't know who the previous owner gave keys to. By rekeying your locks, you can know and control who has access to your home. This can also give you the opportunity to improve the quality of your locks. The Orlando Police Department recommends double-cylinder deadbolt locks.
By rekeying your locks, you can know and control who has access to your home. This can also give you the opportunity to improve the quality of your locks. The Orlando Police Department recommends double-cylinder deadbolt locks.
For even more security, consider installing secondary locks on your windows. A track lock on vinyl or aluminum windows can prevent the window from freely moving up and down. And if you have an attached garage, be sure to lock the house door that accesses the garage.
Read also: Best smart locks for you
Doors
Exterior doors should be solid enough that they're difficult to kick open. They should not have windows that can be broken, giving a burglar access to the lock. Install peepholes at eye level on both your front and back doors, and check them before opening your door to visitors.
Security systems
One of the best ways to deter burglars is with security cameras and home alarm systems. In the KGW survey, burglars said security cameras made them less likely to target a residence. They also said they would leave the property immediately if an alarm sounded.
In the KGW survey, burglars said security cameras made them less likely to target a residence. They also said they would leave the property immediately if an alarm sounded.
As part of your security system, you may also want to install motion-activated lights. Having a well-lit exterior will help keep burglars away at night.
"There is a high positive correlation between having a security system and preventing burglaries," said Lynch. "If you don't have a home security system and you've been burglarized, it would be worth investing in one so you don't become a repeat victim."
These basic tactics are the best research-based methods for preventing burglaries.
Considering buying home security cameras? Check out our coverage of the best security devices on the market, including the best cheap security cameras, the best indoor and outdoor security cameras, the best wireless security cameras, the best video doorbell cameras and much more.
How to Prevent Burglary: 10 Tips from a Burglar
From Spotlight: Home Cleaning Tips That’ll Put More Happy in Your Holidays
Don’t come home to a nightmare and the feeling of being invaded. Here how to stop a house burglary from ever happening.
Here how to stop a house burglary from ever happening.
You come home to an open front door, a ransacked house, and missing valuables. How did a burglar know you’d be gone? How did they get in?
Here are nine tips from a burglar's perspective about how to keep them out. And try these home security tips to prevent burglary, too.
#1 Put Ladders Away
Call me a social climber if you will, but I love ladders. They make it so easy to reach a second-story window. I really love it when upper story openings aren’t wired to a home security system.
So, if you want to keep me out, store your ladder in the basement or a locked garage. And call your security company to wire upper-story windows into your alarm system.
#2 Don't Make Your Trash So Visible
Can’t tell you how much fun I have driving around neighborhoods on trash day (especially after big gift holidays) when the empty boxes on the curb reveal what wonderful new toys you have. That made it possible for me to land a new laptop and a flat-screen TV in one easy trip to your home!
That made it possible for me to land a new laptop and a flat-screen TV in one easy trip to your home!
Next time, break down the boxes and conceal them in the recycling or trash bins.
#3 Keep Shrubs Trimmed
Oh, how I love overgrown shrubs and trees. A wonderful place to hide before I break in and grab all your cool stuff.
Trim back bushes and trees near windows and doors. Make sure entry points to your home are easily visible from the street. I much prefer to work in private. While you’re at it, install motion-sensor lighting.
#4 Be Sure Your Exterior Doors Are Steel
A plain wood-panel door is an invitation. I have no trouble kicking it in.
You may want to install steel-wrapped exterior doors with deadbolts on all your entries. And be sure your windows are locked when you’re away.
#5 Watch Where You Hang Mirrors
You’d be surprised how many homeowners position a mirror in their entry hall so I can see from a window if the alarm system is armed.
A little free advice: Relocate the mirror so your alarm system isn’t visible if someone peers through a window.
#6 Have Someone Attend to Your Home When You're Away
Wow, isn’t it amazing how fast the grass grows? An uncut lawn, unshoveled sidewalks, packages on the porch or in the yard, and shades always closed scream, "I'm empty. Come inside!"
Hire someone you trust to mow or shovel regularly, pick up around the porch and doorstep, open and close various window shades, and turn different lights on and off (or put a few on timers). One more thing: Lock any car you leave in the driveway, or I can use your garage door opener to get in quickly.
#7 Don't Put Valuables in an Easy-Carry Case
I can carry that right out your back door.
You may want to invest in a wall safe, which I rarely attempt to open. Or, rent a lock box at your bank.
It's quite likely that I'm a friend of a friend of yours in the interwebs. And through them, I may discover you're away for the week in Paris, having the time of your life. And I'll have the time of my life ransacking your place.
And I'll have the time of my life ransacking your place.
If only you had known that posting comments and photos of your trip on social networks is fine — as long as you do that after you return, so you won't broadcast your absence.
#9 Inviting People to Your Home to See Stuff You're Selling
You're downsizing. Great! Selling a bunch of stuff like TVs, computers, jewelry. I just have to call you up, and when you invite me to your home, I just grab the items and run.
It's called “robbery by appointment.” If you want to sell high-ticket items to strangers, I suggest you arrange to meet at the parking lot of your local police station. I definitely won’t show up, and you’ll still have your valuables.
For more tips, see our list of low-cost tricks to fool burglars. Did you know there's a gizmo that mimics the glow of a TV?
More in Finances & Taxes
How to protect your phone and account from hacking: instructions from RBC Trends
According to the latest data, the scandalous video of Artem Dziuba leaked online because the football player's phone was hacked. We tell you how to protect your device, social networks and instant messengers, even if there is nothing compromising there
We tell you how to protect your device, social networks and instant messengers, even if there is nothing compromising there
Our phone or chats often contain personal information that attackers can use for their own purposes. For example, card numbers, access to online banks, home address or work correspondence. With a smartphone in hand, it is easy to get logins and passwords for applications, because they are often sent via SMS. Also, scammers can find out about your elderly relatives and deceive them using all known information. Here's how to avoid all of this.
- How to protect your phone
- How to protect your Instagram account
- How to secure your Facebook account
- How to secure WhatsApp
- How to protect Telegram
How to secure your phone
1. Use a complex password. It can be set instead of a 4 or 6 digit unlock PIN.
On iPhone: , go to "Settings" → "Touch ID and passcode" → "Require password: immediately"; "Change password" → "Custom code (letters + numbers)".
For enhanced security, enable reset all data after ten failed attempts.
On Android: "Settings" → "Security" → "Screen Lock", select "Password" as the screen lock method, and set a password of letters and numbers. Then "Settings" → "Security", uncheck "Show passwords".
2. Turn off lock screen notifications. This will prevent attackers from seeing emails and messages - including payment verification codes.
On iPhone: "Settings" → "Password" ("Touch ID and password") → section "Access with screen lock" and "Settings" → "Notifications" → "Show thumbnails" → "No lock".
On Android: "Settings" → "Applications", select the application and uncheck "Show notifications".
3. Turn on two-factor verification on your phone and computer. With two-factor authentication, in addition to the password, you confirm the entry using an SMS code that is sent to the device you connected.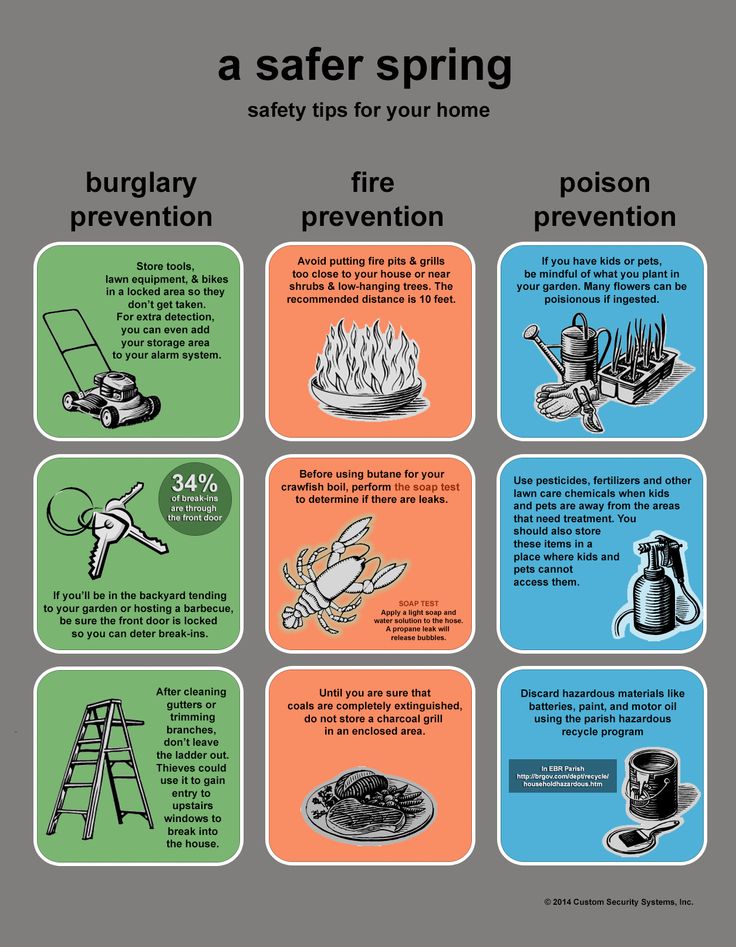 This will prevent outsiders from gaining access to your account.
This will prevent outsiders from gaining access to your account.
On iPhone: Apple ID website → "Two-Factor Authentication" → "On" Then: "Security" → "Verified phone numbers" → "Edit" → "Add phone number with text messaging capability".
On Android: Sign in to your Google Account and follow the instructions on the website.
4. Turn off automatic data synchronization. It is because of her that intimate photos of celebrities often get into the network: hackers hack into their cloud storage from other devices.
On iPhone: Settings → Apple ID, iCloud, Media (or just tap your first and last name at the very top) → iCloud → iCloud Drive and Photos - Off.
On Android: Google Settings → My Location - Tap Off. for Sharing Location Data and Location History. Search & Suggestions - Disable Google Now. "Google Photos" → "Settings" → "Auto upload" - turn off automatic uploading of photos to Google servers.
5. Disable automatic Wi-Fi connection. By default, your phone automatically connects to familiar Wi-Fi networks. However, public networks are often weakly secured and easy to hack. So scammers will get access to all the data on your smartphone.
On iPhone: Settings → Wi-Fi → Select a public network (for example, the one you connected to in the subway or cafe) → Forget this network, as well as Auto-connect and Auto-share - Off Then we return to the list of networks and click "Ask" next to "Request to connect" and "Auto access to the point."
On Android: "Settings" → "Wi-Fi", hold down the desired network, delete it in the menu that appears. In the "Advanced settings" section, uncheck the "Always search for networks" checkbox.
6. Prevent applications from accessing photos / SMS / contacts. Many applications get access to location, photos, social networks, Internet traffic. This can be used by scammers.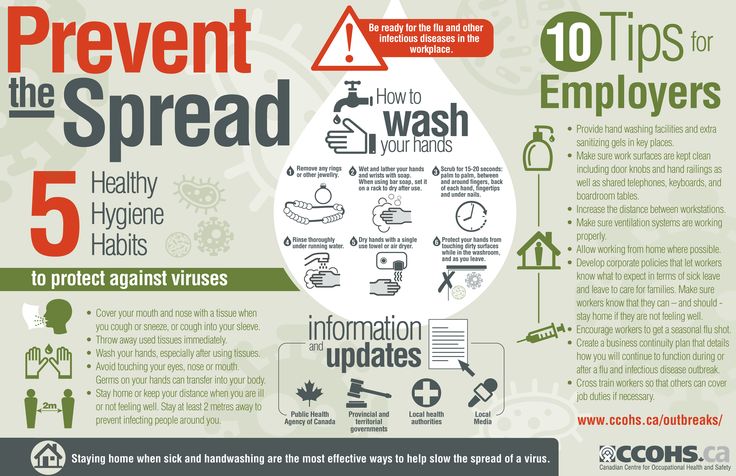
On the iPhone: "Settings" → "Privacy": "Geolocation", "Tracking" and in all applications put Off.
On Android: "Google Settings" → "Connected Apps" - disable all unnecessary.
Other things you can do on iPhone:
1. Disable password autofill. This prevents outsiders from logging into applications and services that you frequently use. "Settings" → "Passwords" → "Autofill passwords" - Off.
2. Disable cookies and autofill in browsers. This is the history of the browser, which stores all the sites that you visited, as well as logins, passwords and settings for them.
For Safari: "Settings" → "Safari" → "Privacy and security" → "No cross-tracking" and "Block all cookies" - On. And also "Autofill" - make sure that everything is Off: storage of data, contacts, credit cards.
For other browsers, check the settings.
What else can be done on Android:
1. Download applications only in the Google Play Store and Yandex.Store . Unlike iOS, Android is an open OS, and any suspicious software can infect a virus, steal your data, or download gigabytes of ads from the Internet. The official store has a Google Play Protect function: it scans 50 billion apps daily on more than 2 billion devices to protect them from viruses and intruders.
Download applications only in the Google Play Store and Yandex.Store . Unlike iOS, Android is an open OS, and any suspicious software can infect a virus, steal your data, or download gigabytes of ads from the Internet. The official store has a Google Play Protect function: it scans 50 billion apps daily on more than 2 billion devices to protect them from viruses and intruders.
"Settings" → "Security", uncheck "Unknown sources" and check the box "Verify applications".
In the same place, in "Settings", make sure that "Play Protection" is active.
2. Encrypt your data. This will help keep them safe even if the phone falls into the wrong hands. To do this, you need to set a password instead of a PIN code and enter it every time you turn on your phone.
Settings → Security → Encrypt phone. Also check the "Encrypt SD card" box.
You can use your Android phone for two-factor authentication through your computer or laptop . This will pair your phone with your computer via Bluetooth to prevent you from visiting phishing sites. You need a computer running Windows 10, macOS, or Chrome OS to set up. Add a Google account to your phone by going to Settings → Accounts → Add Account → Google.
This will pair your phone with your computer via Bluetooth to prevent you from visiting phishing sites. You need a computer running Windows 10, macOS, or Chrome OS to set up. Add a Google account to your phone by going to Settings → Accounts → Add Account → Google.
Then open the Google Chrome browser on your computer.
Go to the "Security" page in Chrome and click "2-Step Verification".
Select "Add Security Key" and then select your phone. You can now sign in to Gmail, Google Cloud, and other Google services using your phone as an additional verification method.
How to secure your Instagram account
1. Set up two-factor authentication .
Go to "Settings" → "Security" → "Two-factor authentication" and select the method of protection: through a special application or via SMS. Now, each time you log into your accounts, you will receive additional codes for verification.
2. Prevent third-party applications from accessing your account.
"Settings" → "Security" → "Apps and sites". Disable all unnecessary applications.
3. Don't forget to remove access from former employees.
If you use Instagram for work, make sure that no former employee has access to your account.
Log in to the application and open your business page. "Settings" → "Roles on the page" → "Existing roles on the page": remove everyone who is no longer working with you.
4. Check who logged into your account.
Settings → Security → Logins. If you see suspicious locations in the list, change your password - someone else may be using your account.
5. Close the profile.
If this is not a work account and you don't earn money from advertising on the blog, it's better to make the profile private. This will at least protect you from spammers.
"Settings" → "Privacy" → "Closed account".
6. Hide your online status.
So no one will know when you are online.
"Settings" → "Privacy" → "Online status".
How to protect your Facebook account
1. Delete personal information.
Facebook can show your age, where you work and where you live, marital status, information about relatives, and even all the places you have visited. If you do not want this information to be used by third-party companies and services, it is better to remove it from the page.
On a PC/laptop:
"Information" → select the desired section and information → "Delete".
In the mobile application:
“View information section” → select the desired section and information → press the pencil and then the cross.
2. Turn off face detection.
Facebook can recognize faces to tag you in photos. You can disable it.
PC/laptop:
In the upper right corner is a triangle, "Settings and privacy" → "Quick privacy settings" → "Manage face recognition" → select "No".
In the mobile application:
Click on the three lines in the lower right corner (the so-called burger menu), then do the same.
3. Restrict apps from accessing your data.
When you log in with Facebook to other services, they get access to your account data: photos, locations, preferences. Don't forget to remove access when you're already signed into the app. iPhone and MacBook users can select "Sign in with Apple" to sign in.
Computer/Laptop:
“Settings and privacy” → “Quick privacy settings” → “Privacy” → “Advanced privacy settings” → “Apps and sites” → check the boxes next to applications and click “Delete”.
On the mobile app:
"Settings and privacy" → "Quick privacy settings" → "Privacy" → "Check basic privacy settings" →
“Your Facebook data settings” → “Apps and websites” → continue in the same way.
4. Restrict access to your posts and personal data.
If you share personal information on the page, it is better to hide it from strangers. Social media profiles are increasingly viewed by HR before interviews and by security before hiring you.
PC/Laptop:
Settings & Privacy → Quick Privacy Settings → Advanced Privacy Settings → Your Activity → Who Can See Your Future Posts? → "Edit" → select "Friends only". There you can also select "Restrict access to old posts" for friends.
In the mobile application: is the same.
How to protect WhatsApp
Both WhatsApp and Instagram belong to the same Facebook. This means, firstly, that the principles of data exchange and account protection are similar. And secondly, that all your correspondence and personal data from chats and Facebook accounts can be used for its own purposes.
1. Do not share your six-digit verification code with anyone.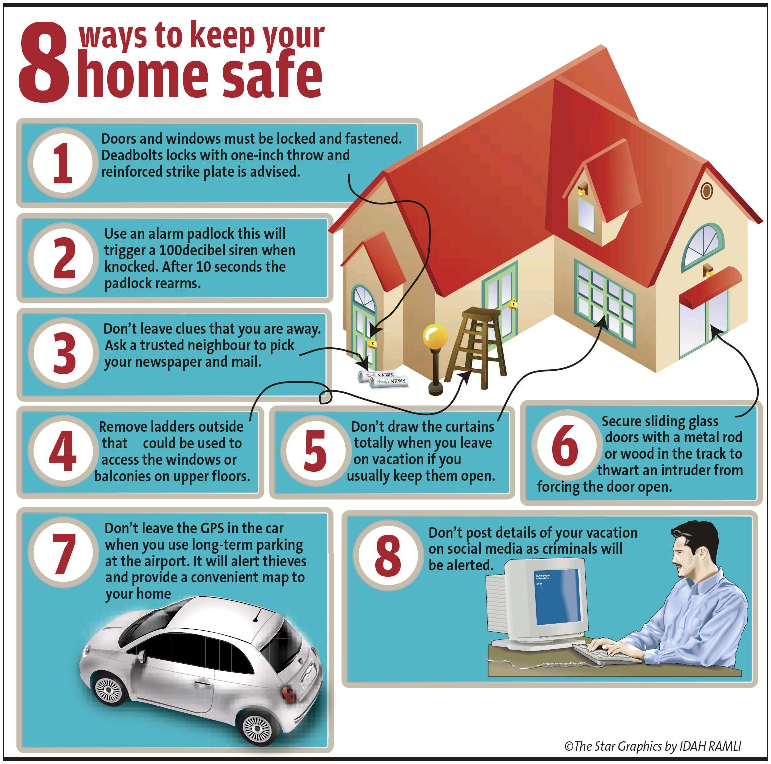
This is the code you receive via SMS to confirm you are logged into WhatsApp on your computer or laptop. This is often used by scammers who can send messages to any user from group chats.
2. Enable two-factor authentication.
"Settings" → "Account" → "Two-Step Verification" → "Enable". Create a PIN and enter your email address so that you can restore or change it.
3. Hide online status, photo and location.
"Settings" → "Account" → "Privacy" → select instead of "Was (a)" "My contacts" or "No one", do the same with "Photo", below - "Geolocation" and other data.
4. Archive chats where you share personal information.
To do this, drag the desired one to the left in the list of chats and select "Archive". It will still be available in the archive, but outsiders will not know about it if they get access to your phone.
5. Turn off message backup
This will protect your communications if someone accesses your Apple or Google account on another device.
For iPhone: Settings → iCloud → WhatsApp - Select Off. Now in the messenger itself: "Settings" → "Chats" → "Backup" → "Automatically" → "Off".
How to secure Telegram
1. Enable two-factor authentication and passcode.
Settings → Privacy → Cloud Password → Set Password. Then go back and select Passcode & Touch ID.
2. Do not click on suspicious links or provide personal information in chats.
Even if it's someone you know. If allegedly Telegram administrators write to you, the profile should have a blue verification checkmark.
3. Send personal data and passwords only in private chats.
Select the desired contact, press. Then click on the profile, select "More" → "Start Secret Chat".
4. Do not forget to log out on your computer or laptop.
Every time you finish working on your personal or, moreover, work computer, log out of your Telegram account.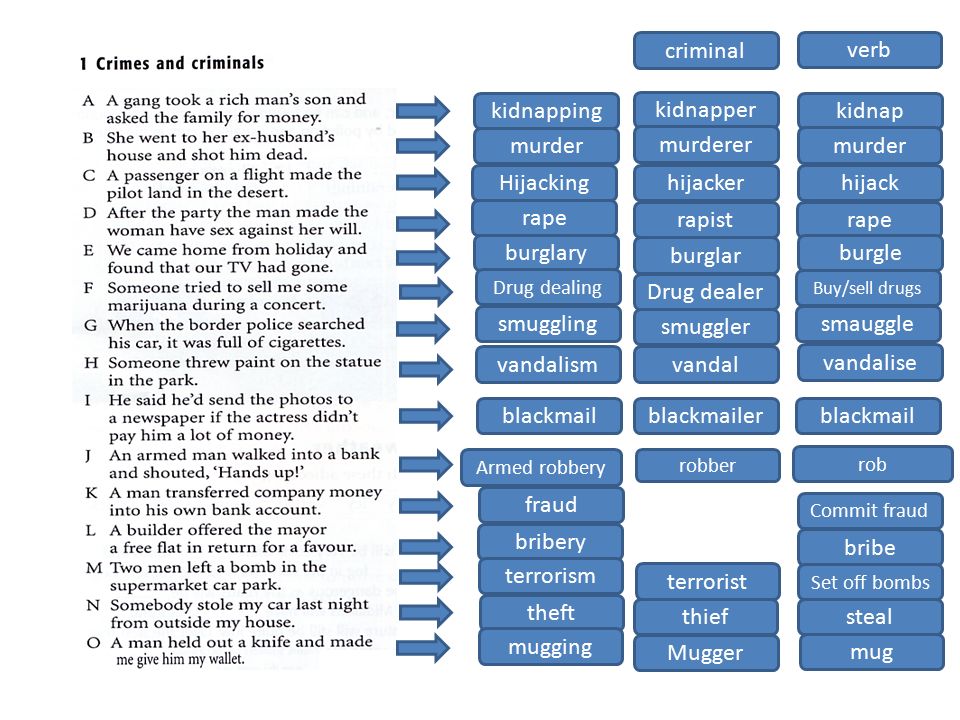 Remember that anyone can access it.
Remember that anyone can access it.
5. Set up automatic deletion of data.
If you have not logged into Telegram for a long time, you can set up automatic deletion of all data after a certain time. “Settings” → “Privacy” → “If I don’t log in” → select the desired period.
Remember the main rules
- Use complex passwords : with letters, numbers and special characters. They must be individual for each device, application and service. In order not to get confused and not to forget, use applications for storing passwords.
- Do not use public Wi-Fi networks. They are poorly protected and attackers can easily access all your data.
- Do not open suspicious links, even from people you know. These could be phishing links or viruses from scammers who hacked into the account of your loved one or colleague.
- Don't share your passwords and accounts.
 Personal or corporate accounts may contain sensitive information. Even if your loved one does not tell anyone about it, scammers can take over their device or account, and then your data will also be at risk.
Personal or corporate accounts may contain sensitive information. Even if your loved one does not tell anyone about it, scammers can take over their device or account, and then your data will also be at risk. - Do not let strangers use your phone or laptop.
- Use two-factor authentication on all devices. For this it is more convenient and safer to use special applications .
- If possible, close your social media profiles . If you do not use social networks for work, it is better to make your profile private. So all the information and posts in it can be seen only by those whom you have added as friends.
Also subscribe to the RBC Trends Telegram channel and stay up to date with current trends and forecasts about the future of technology, economics, education and innovation.
13 ways to protect your account from being hacked
March 15, 2017 Technologies
It's easy to secure your personal data: first, stop using the password 12345 for all accounts. Then it's up to the little things.
Then it's up to the little things.
1. Delete unused accounts
To ensure that active profiles do not suffer due to registration on resources that you do not use, always delete old accounts. The fewer active profiles, the better (if only because you don’t have to keep a dozen logins and passwords in your head).
The same applies to applications you access through social networks. It's much easier to click on the "Login with Facebook*" button than go through the entire registration process, right? Keep track of who and under what conditions you provide access to your profile data. And if you do not use the service, then delete the profile and then check if the site or application still has access to your personal data. Access to Facebook* can be checked here, to a Google account - here.
2. Set up a password manager
These programs seem to not only remember logins and passwords for you, but also generate new ones - ultra-secure ones. And they will also prohibit using the same password for all resources at once. You don't do that, do you?
You don't do that, do you?
3. Use two-step authentication
An intruder, even if he gets hold of your login and password, will not be able to enter your account without SMS confirmation if you set up double authentication. It is available in almost all Microsoft, Apple and Google products. The only inconvenience: even if you are not an attacker, you still have to enter the code from your phone every time to log in to your own accounts.
4. Protect your password change settings
How easy is it for an outsider to change your account password? For example, to reset your Apple ID account password, you need to complete two-factor authentication or answer security questions. To recover your password in Gmail, you will need a mobile phone number or an alternative email address. But all these settings must be set in advance: enter an alternative email for safety net or come up with an answer to a security question known only to you. Right now.
If surveys or comments ask you, "What was your first dog's name?" - shut up like a partisan! In such a simple way, enemies learn the code words for typical secret questions.

5. Check profile activity
Many services remember your activity, and in this case it's even good. This way you will know if someone else has used your account. And some services, like the same Gmail, send a notification to a smartphone and email if they see that they are logging into the account in a region or country that is unusual for the user. You can check your profile activity on Google or Facebook*.
6. Update programs more often
Outdated software is a source of problems and another loophole for a hacker. To make life more difficult for the criminal, try to update the programs as soon as the appropriate notification arrives. Many services have made this process automatic, so you don't have to dig through the settings to find the "Find available updates" button. Just click on the desired button when you receive an alert.
4idroid.com7. Change your passwords regularly
It is normal practice to change your passwords once a year. And don't be lazy to come up with trickier combinations. Altering old passwords is a bad idea.
And don't be lazy to come up with trickier combinations. Altering old passwords is a bad idea.
8. Use a separate email for registrations
Create a separate mailbox for registration on various resources, including social networks. And don't give it to anyone else. Let it be your secret box. And the second email can be safely indicated in work contacts or on business cards.
9. Set up remote control of your smartphone
Settings for iOS and Android devices allow you to block access or delete data from your smartphone remotely. A useful feature if you have lost your smartphone forever or it has been stolen.
iguides.ru10. Use a VPN
VPN is a useful technology that allows you to hide your real location and protect the data you send or receive. Always useful.
11. Set up passwords for your PC and smartphone
Like two-step authentication, this method will add extra steps. But, you must admit, you enter the password to your Microsoft account in three seconds, and attackers will have to tinker much longer.